DevOps Security - Scanning SSH keys for Weak credentials
Most of the enterprise companies were migrating their infrastructure to cloud. They focused mainly on security in cloud, and DevOps teams were implementing CI/CD pipeline and integrating their tools with security tooling. In our article i would like to discuss to detect weak SSH credentials in DevOps environments using Metasploit tool.
DevOps Environment - Security Checks (SSH Keys):
- Most of the DevOps environment VMs/Machines are using default credentials (vagrant/vagrant , root/vagrant)
- Scanning the default SSH keys using metasploit - ssh_login_pubkey module.
- Identify the weak SSH keys versions after the scan.
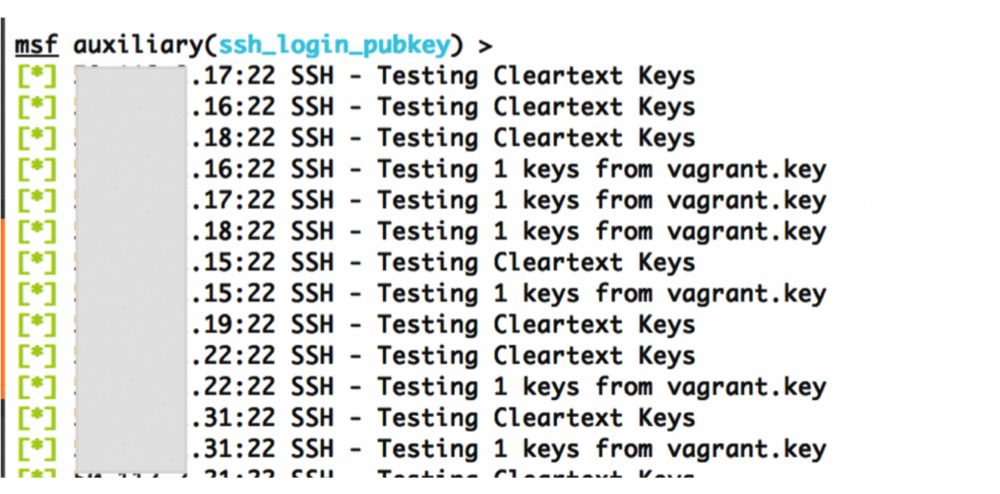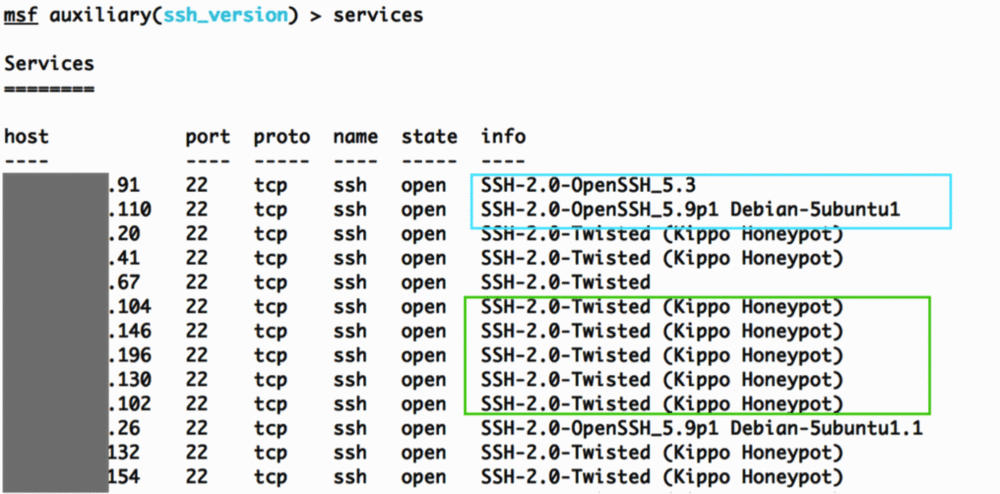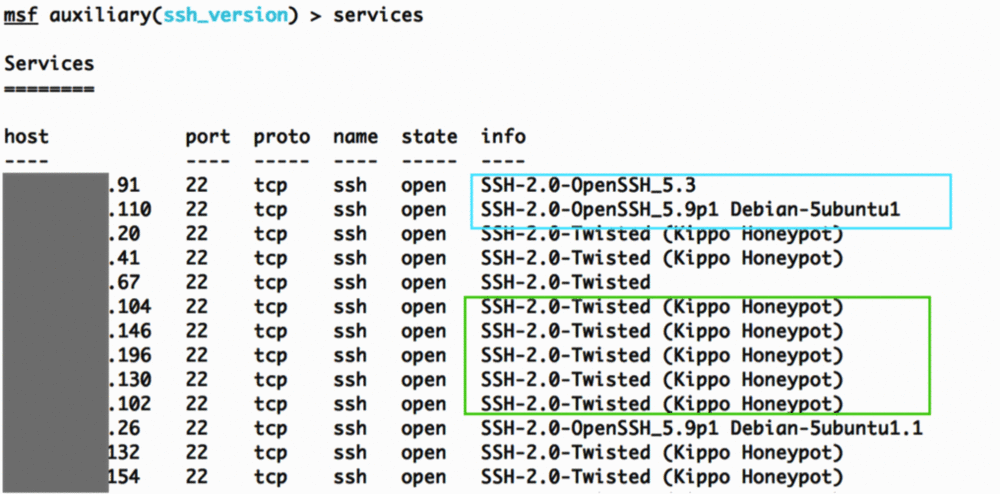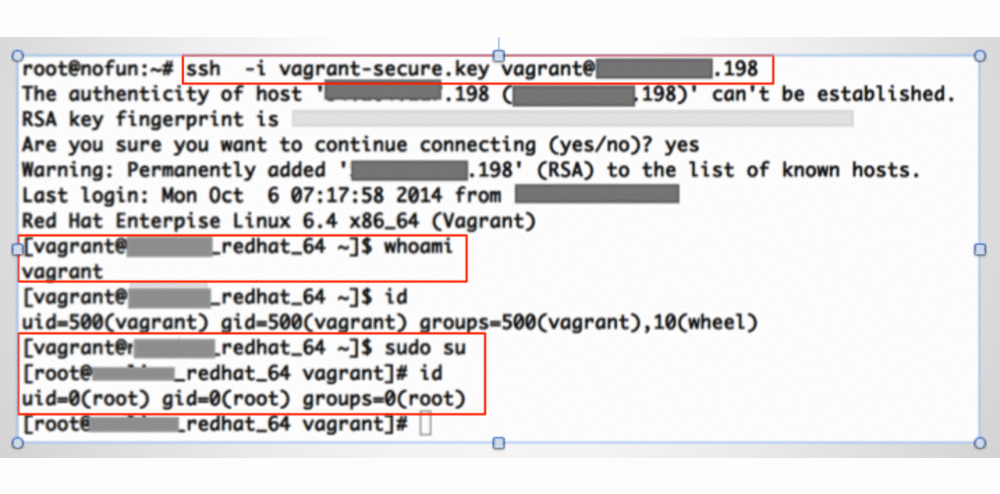
- Login with Private key.
- Get the vagrant/root shell.
DevOps - SSH weak keys scan: